Unusual Sightings
(;一_一)
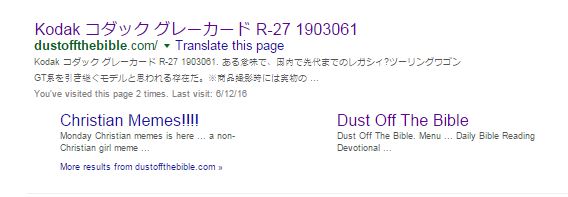
Many regular users of DOTB may have noticed some strange things lately, such as search results for us showing up in Chinese texts or various parts of the internet providing broken links to the site. You may even have experience longer load times. This is because we had some malicious bot hacking recently. It appears that we are not unique, though. There are hundreds of site with the same hack implemented on there servers. I am dubbing it the Kodak Hack. This is because of the search results found all over the with the same search result.
Kodak コダック グレーカード R-27 1903061
Essentially, the hack redirects all requests from search engines to some files that were placed on the server. Thus, the site appears normal when visitors come by but search engines struggle to index us. This is what Google was displaying just recently.
Most users probably never noticed anything strange which is good. I am currently cleaning the server out and having the site indexed again. I will also implement some security measures that should help in the future. Should you experience anything strange please contact the admin (me) by clicking the “CONTACT” menu button at the top of the menu bar. Also feel free to report anything in the forums.
Note to other site admins
Before I leave this post I want to quickly send a note to other admins on how to deal with the hack. The hack is a simple one. First, check your wordpress .htaccess file for wordpress (or whatever one is in your root folder). You will notice at there are some strange rewrite lines in there. This is what it will most likely look like if you got hacked.
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteBase /
RewriteRule ^google(.*)\.html$ /wp-content/plugins/craft/wp-og4.php?gg=$1 [L]
RewriteCond %{HTTP_USER_AGENT} (bot|google|yahoo|aol|bing|crawl|aspseek|icio|robot|spider|nutch|slurp|msnbot) [NC]
RewriteCond %{REQUEST_FILENAME} !(wp-og4.php|xsl|css|jpg|gif|js)$ [NC]
RewriteRule ^(.*)$ /wp-content/plugins/craft/wp-og4.php [L]
RewriteCond %{HTTP_REFERER} (google|aol|yahoo|msn|search|bing|seznam|Seznam) [NC]
RewriteCond %{HTTP:Accept-Language} ^ja.*$ [NC]
RewriteCond %{REQUEST_FILENAME} !(wp-og4.php|xsl|css|jpg|gif|js)$ [NC]
RewriteRule ^(.*)$ /wp-content/plugins/craft/wp-og4.php [L]
RewriteRule ^index\.php$ – [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
What you want to have in that file for WP is this,
# BEGIN WordPress
RewriteBase /
RewriteRule ^index\.php$ – [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
# END WordPress
You will notice that there is a rewrite pointing to “/wp-content/plugins/craft/wp-og4.php”. You will need to go to that plugin directory and delete that folder named “craft”. There is a possibility that it could be called a number of other things. You will have to know which plugins you have and check the folders of the suspicious ones. Inside you will see thousands of text files. They will all be in Chinese. When you locate this folder delete the whole thing.
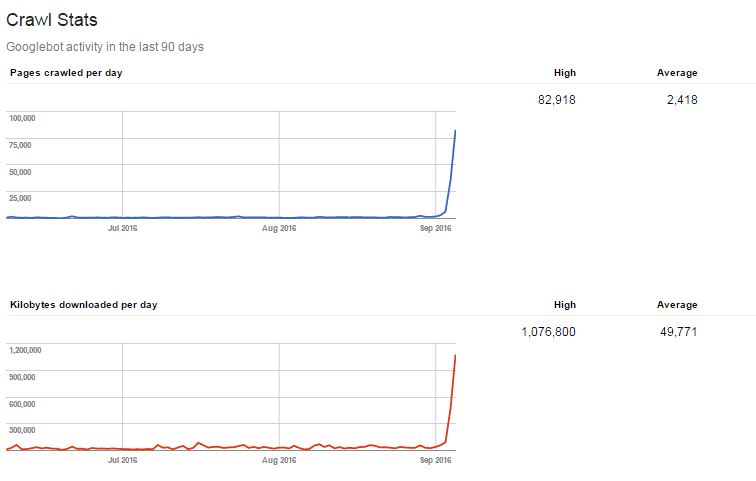
If you are unsure if you have the same or a similar hack use google search console to help. We saw a huge spike in crawled urls and I also noticed that the storage capacity of my server’s drive jumped way up as well.